Sodinokibi Ransomware Now Pushed by Exploit Kits and Malvertising
by CIRT Team
Exploit kit researcher nao_sec has discovered “Sodinokibi” ransomware is now being distributed though malvertising that leads to the RIG exploit kit. Sodinokibi has been making news since the “GandCrab” family of ransomware has retired, but by distributing through hacking sites to replace legitimate software with ransomware, and by hacking into the backends of Managed Service Providers (MSPs).

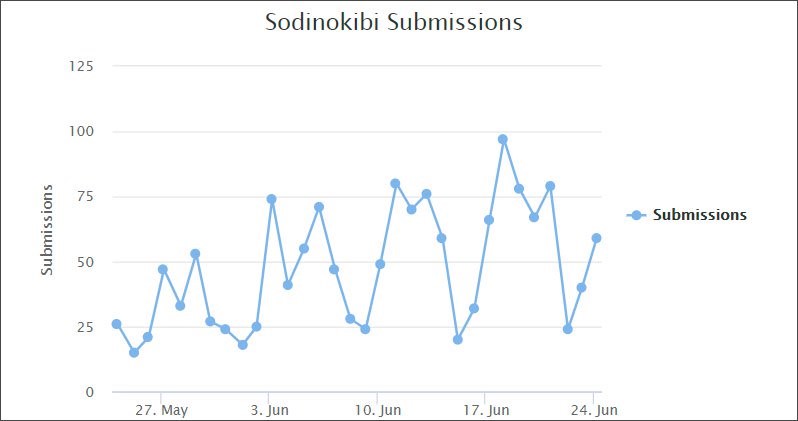
The new use of exploit kits shows Sodinokibi is widening it’s stream of vectors to infect victims with ransomware. According to ID-Ransomware, Sodinokibi has been growing and continues to use similar tactics that GandCrab used in the past.
Recommendation: Malvertising and exploit kit techniques are often updated by threat actors, therefore, keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Reference: https://securelist.com/mobile-banker-riltok/91374/









