“Cybersecurity Professionals Need To Win Every Time, But An Attacker Only Need To Win Once!!!” Now a days VAPT becomes more essential tasks required for the organizations to keep their Cyber/ IT enabled Information Systems secure against the ongoing cyber threats. Performing VAPT is also treated as mandatory requirement by some compliances like as PCI-DSS. Gaps in traditional VAPT “Cost of an Exploitation Always Much...
Read More
Introduction: We are on the verge of the Fourth Industrial Revolution. Smart technologies are taking us to a world that has tremendous opportunities for everybody. With opportunity there comes challenges also. We have to make sure that we overcome challenges to take advantage and grab our fair share of the opportunity. What is IoT? Though almost all of us have heard about IoT, some...
Read More
National Cyber Drill 2020, Bangladesh (NCD 2020) was organized by the BGD e-GOV CIRT on 12-13 December 2020 on the occasion of Digital Bangladesh Day. The drill was to help build the resilience against growing cyber threats. The drill will also help create cyber security awareness and cultivate new crops of cyber experts. The drill was successful in identifying the hidden talents of the budding...
Read More
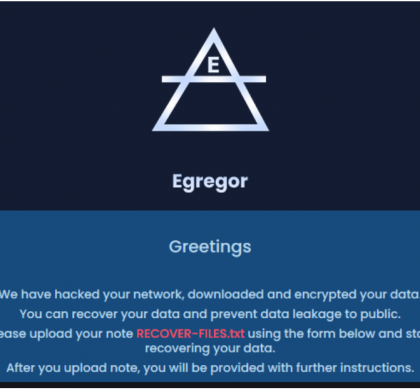
Egregor is a ransomware from the Sekhmet malware family that has been active since the middle of September 2020. The ransomware group hacks into companies, steals information, and finally encrypts all the data. The level of sophistication of their attacks, adaptability to infect such a broad range of victims, and significant increase in their activity suggests that Egregor ransomware operators have been developing their malware...
Read More
On 1st November 2020 Cyber Wales, an UK based cyber security organization, has arranged a webinar to celebrate UAE’s Flag Day, a national campaign to honor the country’s past, present and future. Flag Day is celebrated on November 3, the anniversary of HH Sheikh Khalifa bin Zayed Al Nahyan becoming the president of the UAE in 2004. Objective The aim of sessions is for Cyber...
Read More