Cross-Platform Malware Adwind RAT !!!
by CIRT Team
| Threat Level | Medium |
|---|
Security experts at TrendMicro discovered that the notorious Adwind RAT has resurfaced targeting enterprises in the Aerospace industries worldwide.
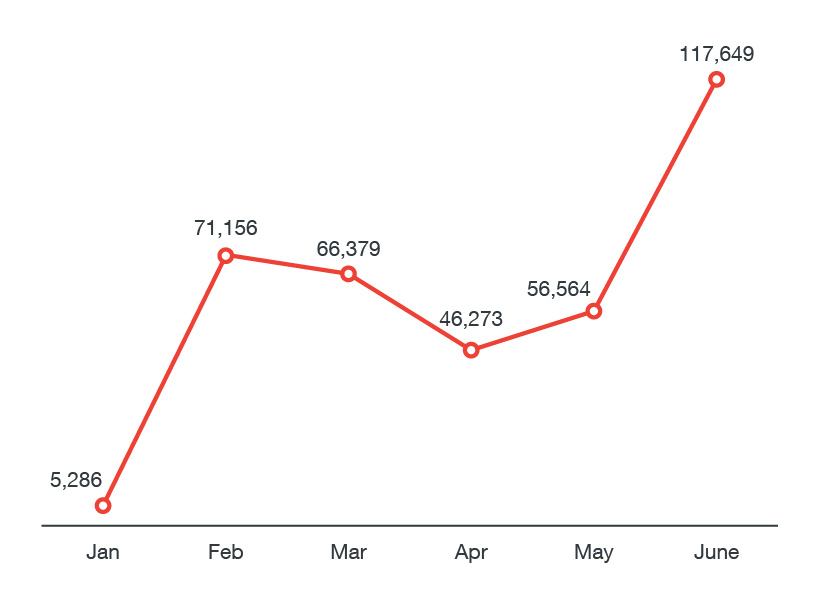
According to trendmicro, From a mere 5,286 in January 2017, it surged to 117,649 in June. It’s notable, too, that JAVA_ADWIND detections from May to June, 2017 increased by 107%, indicating that cybercriminals are actively pushing and distributing the malware. Adwind/jRAT can do the followings :
- Steal credentials
- Record and harvest keystrokes
- Take pictures or screenshots, film and retrieve videos,
- Turn infected machines into botnets to abuse them for destructing online services by carrying out DDoS attacks
- Data gathering and ex-filtrate data
- Collects system’s fingerprints, along with the list of installed antivirus and firewall applications.
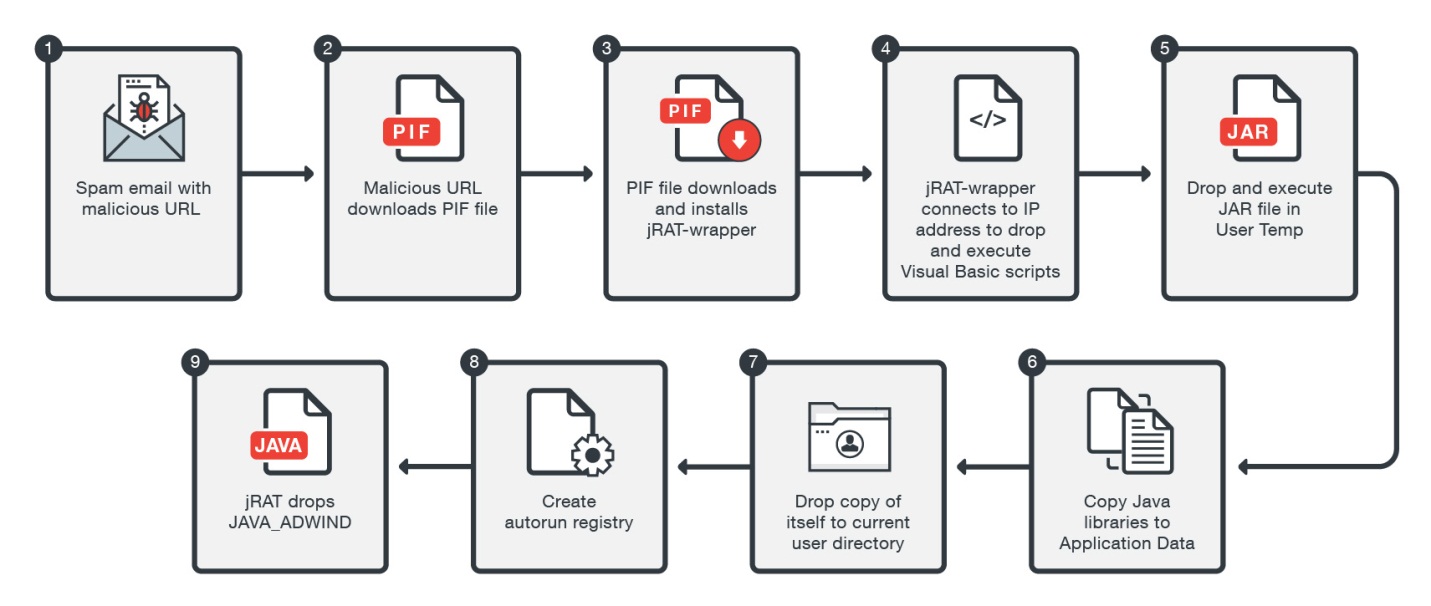
According to a trendmicro, the malicious campaign was noticed on two different occasions. First was observed on June 7 and used a link to divert victims to their .NET-written malware equipped with spyware capabilities, while the second wave was noticed on June 14 and used different domains hosting their malware and command-and-control servers. Both waves apparently employed a similar social engineering tactic to lure victims into clicking the malicious URLs.
The spam email’s message impersonates the chair of the Mediterranean Yacht Broker Association (MYBA) Charter Committee. The spam email’s subject line, “Changes in 2017 – MYBA Charter Agreement”, tries to cause a sense of urgency for potential victims. It uses a forged sender address, (info[@]myba[.]net) and a seemingly legitimate content to trick would-be victims into clicking the malicious URL.
Be sure to stay safe
Adwind is a cross-platform, Java-based malware. This calls for a multilayered approach to security that covers the gateway, endpoints, networks, servers, and mobile devices. The instructions listed below is recommended to be safe from this type of malware.
- IT/system administrators and information security professionals, as well as developers/programmers that use Java should also adopt best practices for using and securing Java and regularly keep it patched and updated
- As this malware is sent over an email, should always be suspicious of uninvited documents sent as email and should never click on links inside those documents unless verifying the source.
- Should keep a good backup routine in place that makes important file copies to an external storage device that is not always connected to your PC.
- Finally, make sure that you run an active & latest anti-virus security suite on your system, and most importantly, always browse the Internet safely.
Source :









