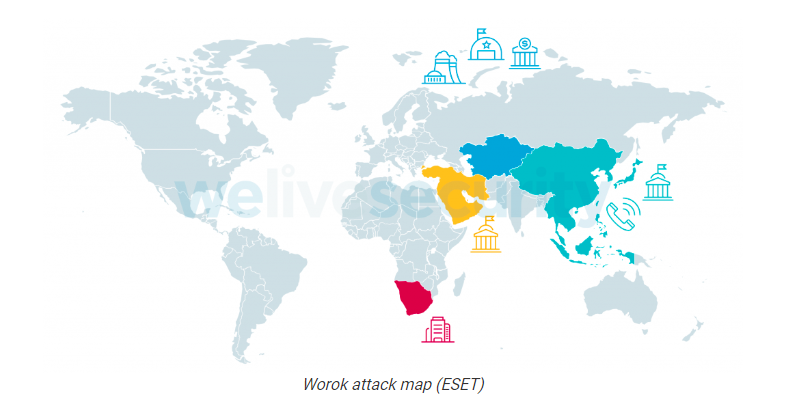
Worok: A New Cyber Espionage Group Targeting Private and Local Government Entities Mostly in Asia
A new cyber espionage threat group that has been previously unknown named Worok and has been observed using undocumented tools targeting private and local government entities mostly in Asia. Based on the report by ESET, the group has been active for at least 2020 and observed a significant break in operation from 2021-05 to 2022-01, but in 2022-02, their operation resumed, targeting an energy company, and a public...
Read More
CVE-2022-40684: Critical Authentication Bypass in FortiOS and FortiProxy
An authentication bypass using an alternate path or channel vulnerability [CWE-288] in FortiOS, FortiProxy and FortiSwitchManager may allow an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests. Exploitation Status: Fortinet recommends immediately validating systems against the following indicator of compromise in the device’s logs:user=”Local_Process_Access” Affected ProductsFortiOS version 7.2.0 through 7.2.1FortiOS version 7.0.0 through 7.0.6FortiProxy version 7.2.0FortiProxy version...
Read More
by CIRT Team
Facebook warns about 400 password-stealing apps! Camera, beauty, VPN apps on the list
The tech giant has uncovered more than 400 malicious Android and iOS apps this year which steal usernames and passwords. 45 out of the 400 apps it found were on iOS, while the rest were on Android. They masquerade themselves as popular services like photo editors, games and VPNs to trick people into downloading them. How do these malicious apps work? Apart from displaying fun...
Read More
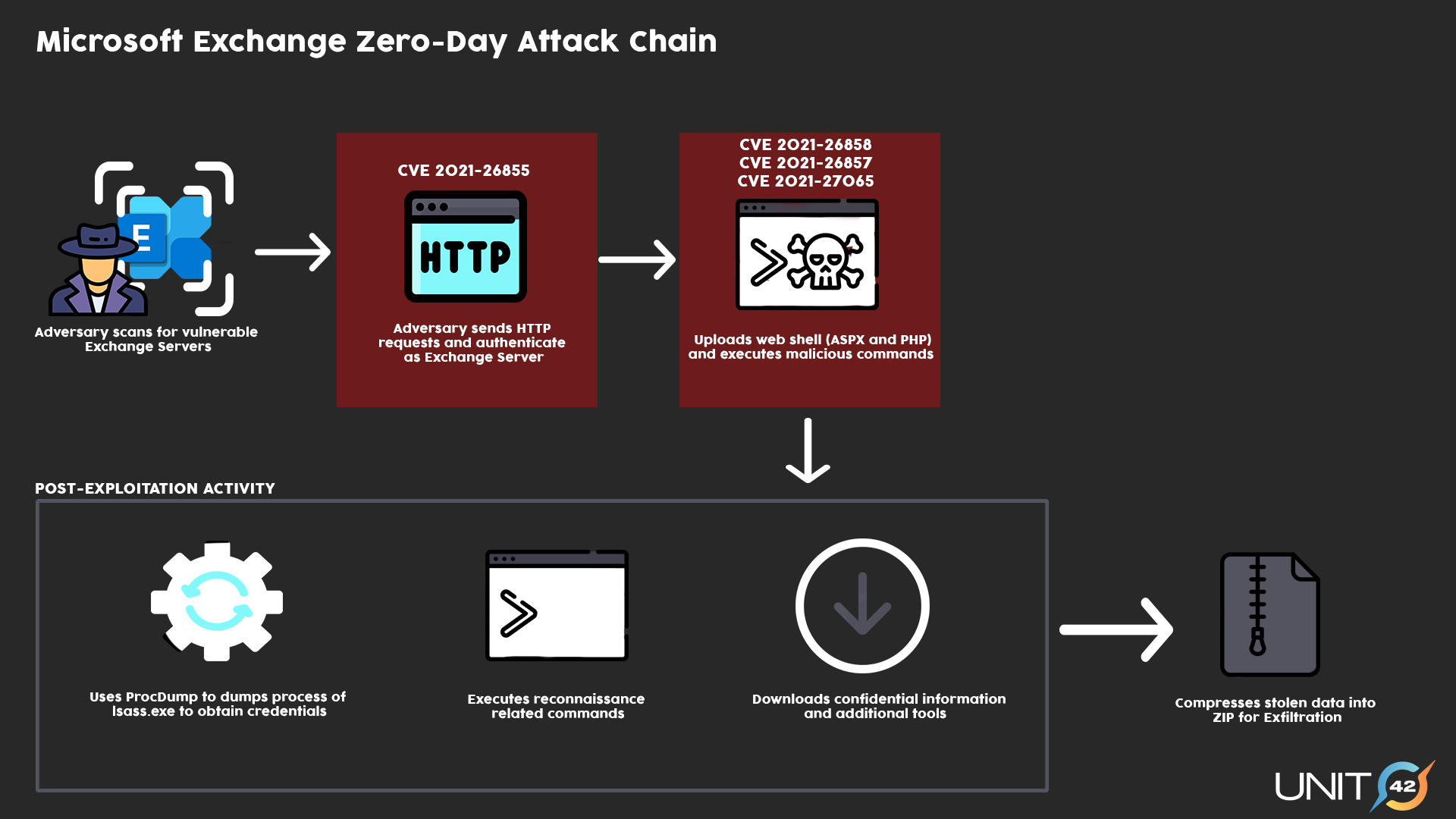
Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082
Microsoft has confirmed that two reported zero-day vulnerabilities in Microsoft Exchange Server 2013, 2016, and 2019. The first one, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, and the second one, identified as CVE-2022-41082, allows Remote Code Execution (RCE) when PowerShell is accessible to the attacker. From the note Microsoft added, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should...
Read More

North Korean Hackers Weaponizing Open-Source Software in Latest Cyber Attacks
Hackers backed by the North Korean government are weaponizing well-known pieces of open source software in an ongoing campaign that has already succeeded in compromising “numerous” organizations in the media, defense and aerospace, and IT services industries, Microsoft said on Thursday. ZINC—Microsoft’s name for a threat actor group also called Lazarus, which is best known for conducting the devastating 2014 compromise of Sony Pictures Entertainment—has been...
Read More

Microsoft confirms two Exchange Server zero days are being used in cyberattacks
Microsoft confirmed it is investigating two zero days affecting its Exchange Server software late Thursday following a report from Vietnamese cybersecurity firm GTSC that the vulnerabilities are being exploited in the wild. GTSC said it discovered the issues in August while doing security incident monitoring and response, then reported the issue to Microsoft’s Zero Day Initiative, which confirmed the bugs. The attacks GTSC reported chain together the two vulnerabilities. ...
Read More

Critical Vulnerability in Sophos Firewall
Sophos warned today that a critical code injection security vulnerability in the company’s Firewall product is being exploited in the wild. “Sophos has observed this vulnerability being used to target a small set of specific organizations, primarily in the South Asia region,” the security software and hardware vendor warned. “We have informed each of these organizations directly. Sophos will provide further details as we continue...
Read More

Researchers Uncover a New Metador APT Targeting Telcos, ISPs, and Universities.
Executive Summary SentinelLabs researchers uncovered a never-before-seen advanced threat actor we’ve dubbed ‘Metador’. Metador primarily targets telecommunications, internet service providers, and universities in several countries in the Middle East and Africa. The operators are highly aware of operations security, managing carefully segmented infrastructure per victim, and quickly deploying intricate countermeasures in the presence of security solutions. Metador’s attack chains are designed to bypass native security...
Read More

High-Severity Firmware Security Flaws Left Unpatched in HP Enterprise Devices
A number of firmware security flaws uncovered in HP’s business-oriented high-end notebooks continue to be left unpatched in some devices even months after public disclosure. Binarly, which first revealed details of the issues at the Black Hat USA conference in mid-August 2022, said the vulnerabilities “can’t be detected by firmware integrity monitoring systems due to limitations of the Trusted Platform Module (TPM) measurement.” Firmware flaws can have serious implications...
Read More
Travel Industry Recovering From Covid Turbulence, Grounded By Cyberattacks
Cybercrime Activities At A Glance Introduction The Aviation industry is a critical, strategic, and economically important sector for any nation. The pandemic-struck industry has started showing signs of gradual recovery after two years of volatility, however, attaining the pre-COVID global travel figures seems still farfetched until mid-2023. Amidst epidemic chaos, the Aviation industry steered itself towards embracing technology to reduce human dependence and make a...
Read More









