![2019 CWE Top 25 Most Dangerous Software Errors [mitre]](https://www.cirt.gov.bd/wp-content/uploads/2019/09/2019CWETop25.png)
by CIRT Team
2019 CWE Top 25 Most Dangerous Software Errors [mitre]
Introduction The Common Weakness Enumeration (CWE™) Top 25 Most Dangerous Software Errors (CWE Top 25) is a demonstrative list of the most widespread and critical weaknesses that can lead to serious vulnerabilities in software. These weaknesses are often easy to find and exploit. They are dangerous because they will frequently allow adversaries to completely take over execution of software, steal data, or prevent the software...
Read More

by CIRT Team
Security Tip (ST19-003) Privacy and Mobile Device Apps
What are the risks associated with mobile device apps? Applications (apps) on your smartphone or other mobile devices can be convenient tools to access the news, get directions, pick up a ride share, or play games. But these tools can also put your privacy at risk. When you download an app, it may ask for permission to access personal information—such as email contacts, calendar inputs,...
Read More
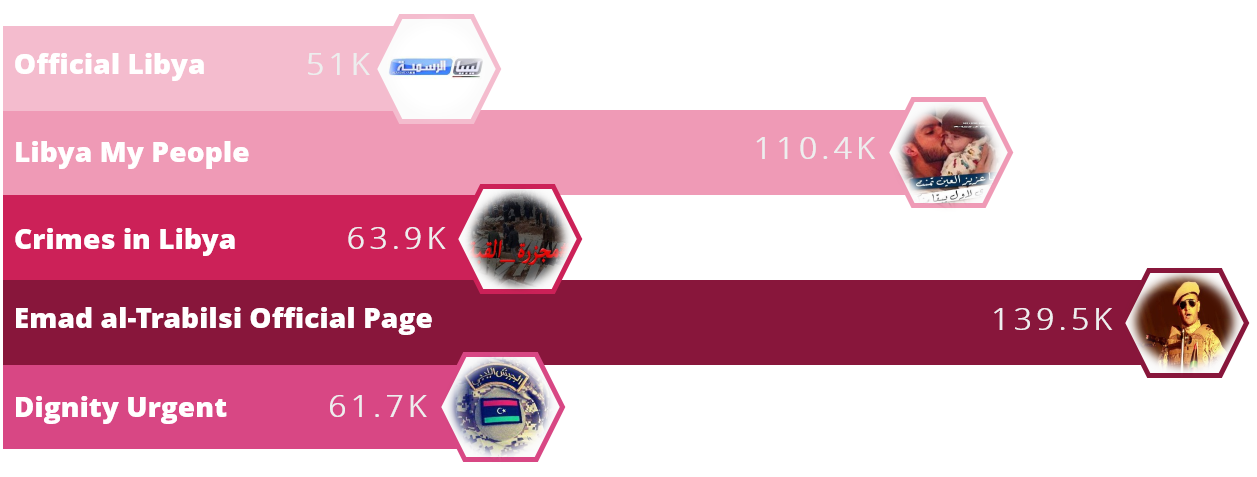
by CIRT Team
Operation Tripoli
A large-scale campaign has been distributing malware on Facebook for an unspecified number of years primarily targeting the country of Libya, according to Check Point researchers. The threat actors behind this campaign are utilizing the geopolitical and political pages themed around Libya that attempt to convince individuals to download malicious files. Researchers identified more than 30 Facebook pages distributing malicious links and some of the...
Read More
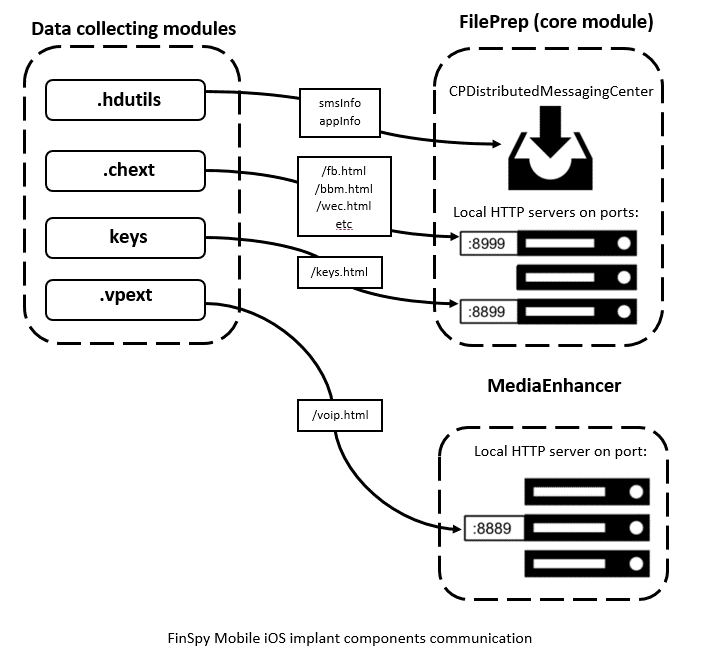
by CIRT Team
New FinSpy iOS and Android implants revealed ITW
FinSpy is spyware made by the German company Gamma Group. Through its UK-based subsidiary Gamma International Gamma Group sells FinSpy to government and law enforcement organizations all over the world. FinSpy is used to collect a variety of private user information on various platforms. Its implants for desktop devices were first described in 2011 by Wikileaks and mobile implants were discovered in 2012. Since then...
Read More
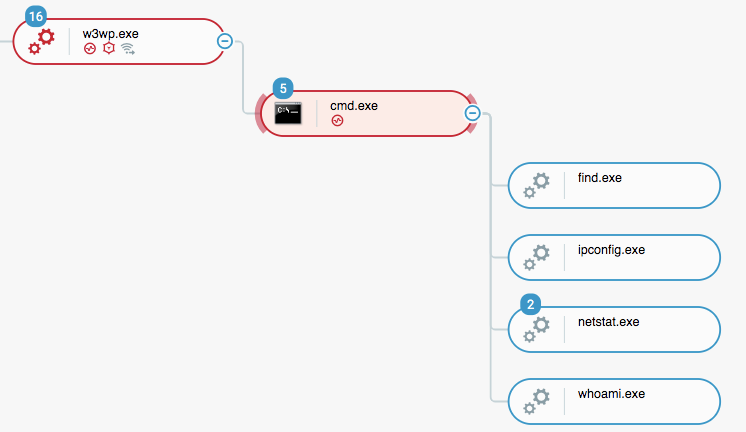
by CIRT Team
Operation Soft Cell: A Worldwide Campaign Against Telecommunications Providers
An advanced, persistent attack targeting telecommunication providers, active since at least 2012, according to Cybereason researchers. The attack, dubbed Operation Soft Cell, was aiming to obtain all data stored in the active directory of a large telecommunications provider, compromising usernames and passwords within the organization, as well as billing information, call detail records, credentials, email servers, and personal identifiable information. The attack consisted of customized...
Read More
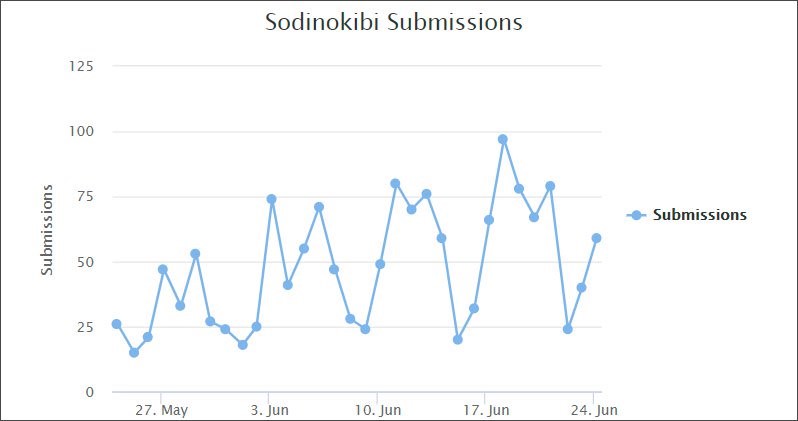
by CIRT Team
Sodinokibi Ransomware Now Pushed by Exploit Kits and Malvertising
Exploit kit researcher nao_sec has discovered “Sodinokibi” ransomware is now being distributed though malvertising that leads to the RIG exploit kit. Sodinokibi has been making news since the “GandCrab” family of ransomware has retired, but by distributing through hacking sites to replace legitimate software with ransomware, and by hacking into the backends of Managed Service Providers (MSPs). The new use of exploit kits shows Sodinokibi...
Read More
by CIRT Team
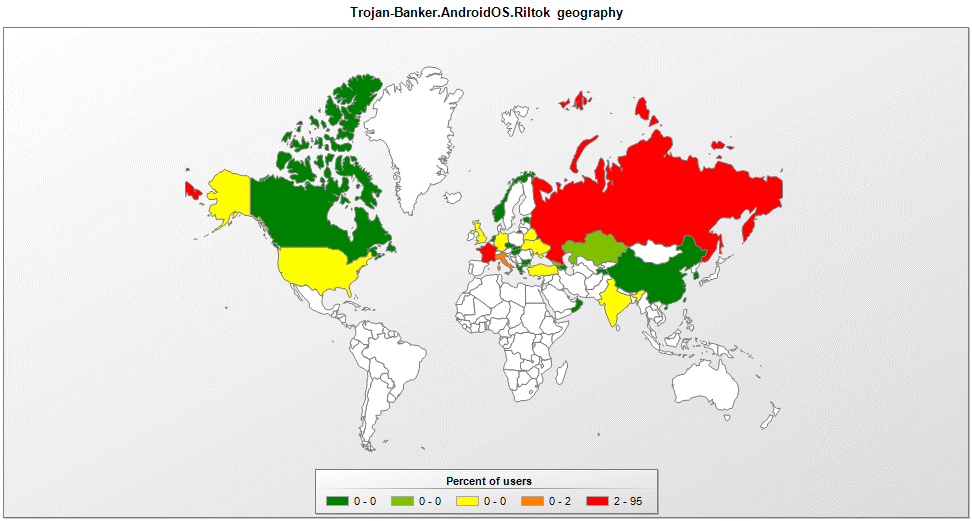
Riltok mobile Trojan: A banker with global reach
Kaspersky Lab researchers have identified a new variant of the Riltok mobile banking trojan that has been in operation since March 2018. The actors distributing Riltok have primarily focused on targeting individuals that reside in Russia, but versions for markets in France, Italy, Ukraine, and the United Kingdom have been detected in 2019. The trojan is distributed via SMS with a malicious link pointing to...
Read More
by CIRT Team
বিজিপি রুট লিক (BGP Route Leak) এবং প্রতিকারে সম্ভাব্য করণীয়
বিজিপি রুট লিক (BGP Route Leak) কি? ইন্টারনেট ইঞ্জিনিয়ারিং টাস্ক ফোর্স (আইইটিএফ/ IETF) এর RFC 7908 মতে বিজিপি রুট লিক (BGP Route Leak) নিমক্ত ভাবে সংজ্ঞায়িত করা হয়েছেঃ “The propagation of routing announcement(s) beyond their intended scope. That is, an announcement from an Autonomous System (AS) of a learned BGP route to another AS is in violation of the intended policies of the receiver, the...
Read More
by CIRT Team
High Commissioner of India, Dhaka visits BGD e-GOV CIRT Operations Center
High Commissioner of India, Ms Riva Ganguly Das has visited BGD e-GOV CIRT Security operations center on 19 June, 2019. She visited different components of BGD e-GOV CIRT and got briefed about the daily activities of security operations center, cycler censor activities, cyber range lab and digital forensic lab. Hon’ble state Minister Zunaid Ahmed Palak MP, Secretary of ICT Division N M Zeaul Alam, Executive...
Read More

by CIRT Team
BGD e-GOV CIRT has topped on Cybersecurity Drill – arranged by Sandia National Laboratories, US
Sandia National Laboratories Center for Global Security and Cooperation (operated by National Technology and Engineering Solutions of Sandia, LLC.) – Operated for the United States Department of Energy arranged two days hands on training on the “Countering DPRK Cyber Operations Workshop” held on 11 – 1 2 June 2019 at Dhaka, Bangladesh. The purpose of the workshop was to understand and prevent DPRK illicit cyber...
Read More









