Welcome to the McAfee Labs 2018 Threats Predictions Report. We find ourselves in a highly volatile stage of cybersecurity, with new devices, new risks, and new threats appearing every day. In this edition, we have polled thought leaders from McAfee Labs and the Office of the CTO. They offer their views on a wide range of threats, including machine learning, ransomware, serverless apps, and privacy...
Read More
Description: Apple has released a supplemental security update to address a vulnerability in macOS High Sierra 10.13. Impact: An attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: http://www.kb.cert.org/vuls/id/113765 https://support.apple.com/en-us/HT208315
The Exim Internet mail message transfer agent warned of flaws through the public bug tracker, sys admins have to apply the workaround asap. Exim is a message transfer agent (MTA) developed at the University of Cambridge for use on Unix systems connected to the Internet, it is the most popular MTA on the Internet. The Internet mail message transfer agent warned of flaws through the public bug tracker, an unfortunate choice...
Read More
Many Linux distributions are at risk due to a recently disclosed flaw in systemd: a flaw in its DNS resolver could cause a denial-of-service attack on vulnerable systems. The vulnerability is exploited by having the vulnerable system send a DNS query to a DNS server controlled by the attackers. The DNS server would then return a specially crafted query, causing systemd to enter an infinite loop that pins...
Read More
Organizations believe that today’s cyber threat landscape places them at high risk of cyber attacks. The EY survey of nearly 1,200 C-level leaders of the world’s largest and most recognized organizations examines some of the most urgent concerns about cybersecurity and their efforts to manage them. Findings show that 56% of those surveyed are making or planning to make changes to their strategies and plans due to the increased...
Read More
If you thought 2017 was a dire year for data breaches, wait until 2018. The Information Security Forum (ISF), a global, independent information security body that focuses on cyber security and information risk management, forecasts an increase in the number and impact of data breaches, thanks in large part to five key global security threats that organizations will face in 2018. “The scope and pace...
Read More
Besides being a useful tool to study human-computer interaction, keystroke logging or keylogging is one of the most dangerous cyber threats for online users. Designed to covertly log everything a user types using the keyboard, keyloggers can silently steal and pass on your sensitive information to cybercriminals. Not just the websites you browse or the queries you google on, but your confidential details like online...
Read More
HP said it would release firmware patches later this week for several security bugs reported to the company by various cyber-security experts. The firmware patches address a slew of bugs, among which the most severe is a remote code execution (RCE) flaw discovered and reported by Stephen Breen of NTT Security. The RCE bug (CVE-2017-2750) affects HP’s top-of-the-line enterprise printer series such as LaserJet and...
Read More
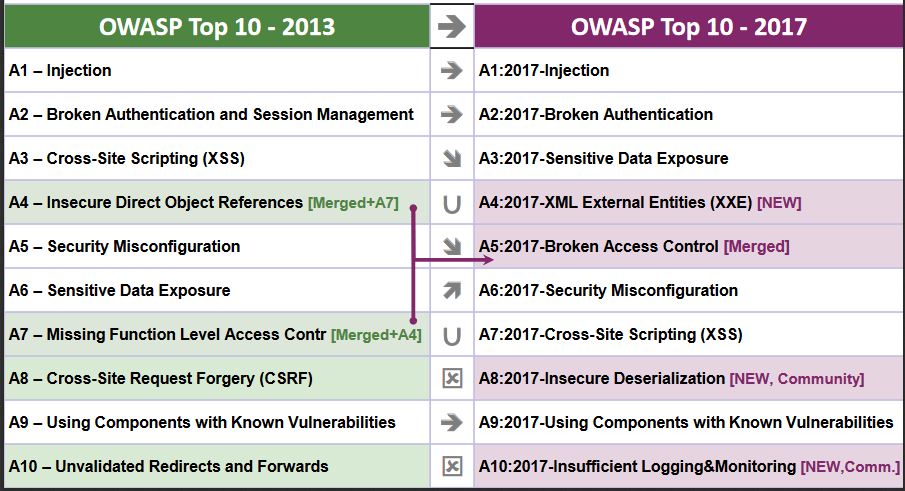
The Open Web Application Security Project (OWASP) has officially released its Top 10 most critical web application security risks four years after its last update, in 2013. As in previous years, injection remained the top application security risk, but there has been some shuffling in the ranking, with the appearance of three newcomers — XML External Entities (XXE), Insecure Deserialization and Insufficient Logging & Monitoring....
Read More
Description: An authentication bypass vulnerability in Juniper Networks Junos Space Network Management Platform may allow a remote unauthenticated network based attacker to login as any privileged user. This issue only affects Junos Space Network Management Platform 17.1R1 without Patch v1 and 16.1 releases prior to 16.1R3 Impact: An attacker can exploit this issue to bypass the authentication mechanism and perform unauthorized actions. This may lead...
Read More