If you own an Android device, it might already be infected with a dangerous malware called Agent Smith, named after the menacing character in The Matrix. The malware’s already infected around 25 million Android devices globally, with thousands in Australia thought to be compromised. Here’s what you need to know. What is Agent Smith? As reported on Checkpoint, Agent Smith has been invading devices via dodgy third-party...
Read More
What are the risks associated with mobile device apps? Applications (apps) on your smartphone or other mobile devices can be convenient tools to access the news, get directions, pick up a ride share, or play games. But these tools can also put your privacy at risk. When you download an app, it may ask for permission to access personal information—such as email contacts, calendar inputs,...
Read More
Description: Cisco has released security updates to address a vulnerability in Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software. A remote attacker could exploit this vulnerability to cause a denial-of-service condition. Impact: A remote attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190710-asa-ftd-dos
Description: Atlassian has released security updates to address a vulnerability affecting Jira Server and Jira Data Center. A remote attacker could exploit this vulnerability to take control of an affected system. Paragraph Impact: A remote attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://confluence.atlassian.com/jira/jira-security-advisory-2019-07-10-973486595.html https://cyber.gc.ca/en/alerts/atlassian-confluence-security-advisory
If you think that the media files you receive on your end-to-end encrypted secure messaging apps can not be tampered with, you need to think again. Security researchers at Symantec yesterday demonstrated multiple interesting attack scenarios against WhatsApp and Telegram Android apps, which could allow malicious actors to spread fake news or scam users into sending payments to wrong accounts. Dubbed “Media File Jacking,” the...
Read More
Overview Throughout 2018, Proofpoint researchers observed threat actors increasingly distributing downloaders, backdoors, information stealers, remote access trojans (RATs), and more as they abandoned ransomware as their primary payload. In November 2018, TA505, a prolific actor that has been at the forefront of this trend, began distributing a new backdoor we named “ServHelper”. ServHelper has two variants: one focused on remote desktop functions and a second that...
Read More
Summary The National Cybersecurity and Communications Integration Center (NCCIC), part of the Cybersecurity and Infrastructure Security Agency (CISA), is aware of a global Domain Name System (DNS) infrastructure hijacking campaign. Using compromised credentials, an attacker can modify the location to which an organization’s domain name resources resolve. This enables the attacker to redirect user traffic to attacker-controlled infrastructure and obtain valid encryption certificates for an...
Read More
Recently, we had an incident response involving the malware DNSPIONAGE. At CERT-OPMD, we thought it would be interesting to share our observations. Mainly, we could observe quietly common actions and tools as described in infography below. HOW DNSPIONAGE INFECTS TARGETS In this blogpost, we will not describe and analyse again the dropper, because Talos did a great job here : https://blog.talosintelligence.com/2018/11/dnspionage-campaign-targets-middle-east.html But we will focus in...
Read More
Mozilla has finally introduced a mechanism to let Firefox browser automatically fix certain TLS errors, often triggered when antivirus software installed on a system tries to intercept secure HTTPS connections. Most Antivirus software offers web security feature that intercepts encrypted HTTPS connections to monitor the content for malicious web pages before it reaches the web browser. To achieve this, security software replaces websites’ TLS certificates...
Read More
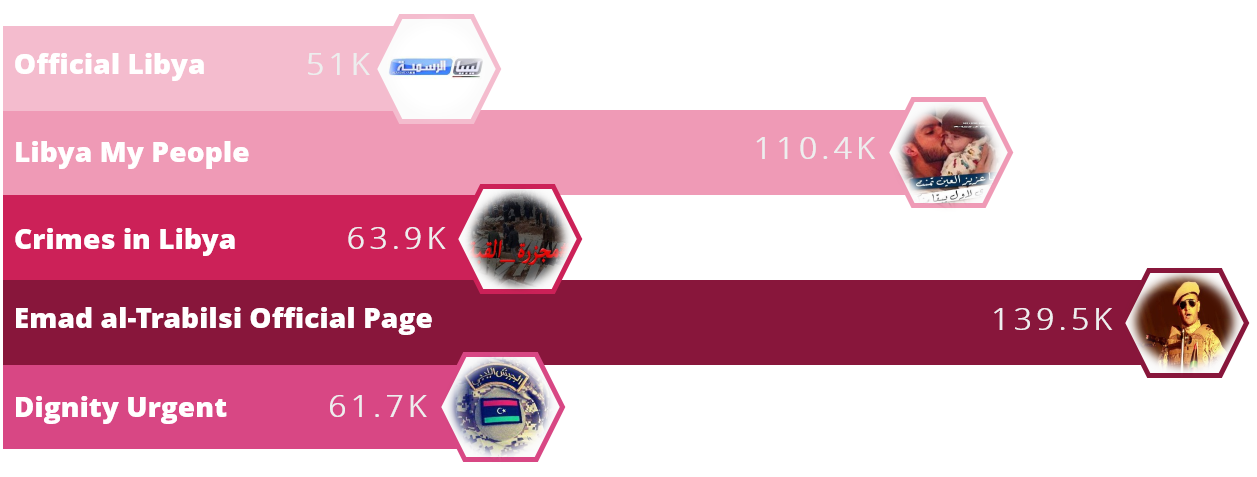
A large-scale campaign has been distributing malware on Facebook for an unspecified number of years primarily targeting the country of Libya, according to Check Point researchers. The threat actors behind this campaign are utilizing the geopolitical and political pages themed around Libya that attempt to convince individuals to download malicious files. Researchers identified more than 30 Facebook pages distributing malicious links and some of the...
Read More