Description: Mozilla has released a security update to address vulnerabilities in Thunderbird. An attacker could exploit some of these vulnerabilities to take control of an affected system. Impact: A remote attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://www.mozilla.org/en-US/security/advisories/mfsa2019-35/
Description: The Samba Team has released security updates to address vulnerabilities in multiple versions of Samba. An attacker could exploit some of these vulnerabilities to obtain sensitive information. Impact: A remote attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://www.samba.org/samba/security/CVE-2019-10218.html https://www.samba.org/samba/security/CVE-2019-14833.html https://www.samba.org/samba/security/CVE-2019-14847.html
Description: Apple has released security updates to address vulnerabilities in multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system. The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review the Apple security pages for the following products and apply the necessary updates. Impact: A remote attacker could exploit this vulnerability to take control of...
Read More
Nearly 1.3 million debit and credit card data of Indian banking customers that can fetch up to $130 million for cybercriminals are available on Dark Web for open sale. According to ZDNet, the cards’ details is available on Joker’s Stash — one of the oldest card shops on the dark web which is known to be the place where major hackers sell card dumps. The...
Read More
We’re already aware that data breaches are on a constant rise these days. Hackers are making use of stealthy creative ways to get access to our sensitive data. Kaspersky, a Russia-based cybersecurity firm, revealed recently that it has discovered samples of ‘Dtrack’ malware from enterprises across Indian states including Maharashtra, Karnataka and Telangana, according to a report by IANS. The Dtrack malware is kind of a...
Read More
NordVPN, a virtual private network provider that promises to “protect your privacy online,” has confirmed it was hacked. The admission comes following rumors that the company had been breached. It first emerged that NordVPN had an expired internal private key exposed, potentially allowing anyone to spin out their own servers imitating NordVPN. VPN providers are increasingly popular as they ostensibly provide privacy from your internet provider...
Read More
The KRACK attack was published by two Belgian researchers in October 2017. The attacks are based on the weaknesses in the WPA2 protocol used in modern Wi-Fi devices. The weakness can be exploited by the attackers using key reinstallation attacks if the victim resides within the network. Successful exploitation of the attack allows attackers to steal sensitive details such as credit card numbers, passwords, chat...
Read More
Facial recognition systems are bio-metric technologies capable of identifying or verifying a person from a digital image or a video frame from a video source. Facial recognition can identify a person by analyzing patterns based on the person’s facial textures and shape. Facial recognition is said to be started in the 60s when Woodrow Wilson Bledsoe, one of the founders of artificial intelligence, manually classified faces...
Read More
It‘s a great pleasure to share my experience of working with Oxygen Forensic Detective, which was a crucial tool in solving one of my cases. A father of a minor girl contacted me, worried his daughter was in suspicious society and probably had been consuming marijuana. His wife accidentally found traces of a substance which looked and smelled like marijuana in his daughter‘s clothes and...
Read More
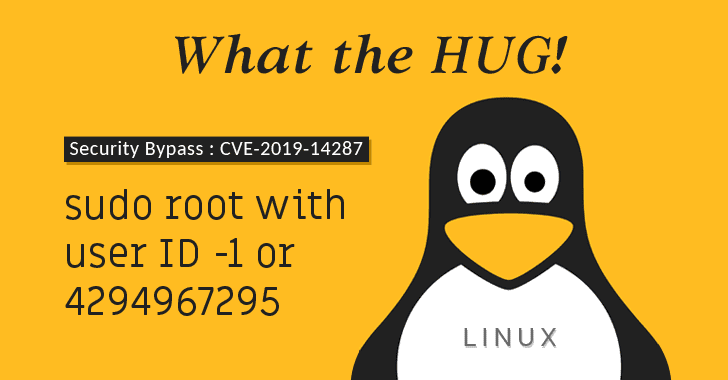
লিনাক্স কিংবা ইউনিক্স সিস্টেম নিয়ে যারা কাজ করেন তাদের কাছে sudo(super user do/substitute user do) অত্যন্ত পরিচিত একটা শব্দ। সিস্টেম আপডেট দিতে যাবেন আপনার sudo লাগবে। অ্যাপ ইন্সটল করবেন sudo লাগবে। বলতে গেলে sudo ছাড়া ইউনিক্স দুনিয়াতে আপনি প্রায় অচল হয়ে পরতে পারেন। ইউনিক্স কিংবা ইউনিক্সের মতন অপারেটিং সিস্টেমে, sudo প্রোগ্রামের মাধ্যমে মূলত একজন ইউজার অন্য ইউজারের সিকিউরিটি প্রিভিলেজ ব্যবহার(Runas) করে কোন কমান্ড এক্সিকিউট করার...
Read More