Description: Multiple vulnerabilities in the Cisco Webex Network Recording Player and Cisco Webex Player could allow an unauthenticated, remote attacker to execute arbitrary code on the system of a targeted user. An attacker could exploit these vulnerabilities by sending a user a link or email attachment containing a malicious ARF (Advanced Recording Format) or WRF (Webex Recording Format) file via a link or an email...
Read More
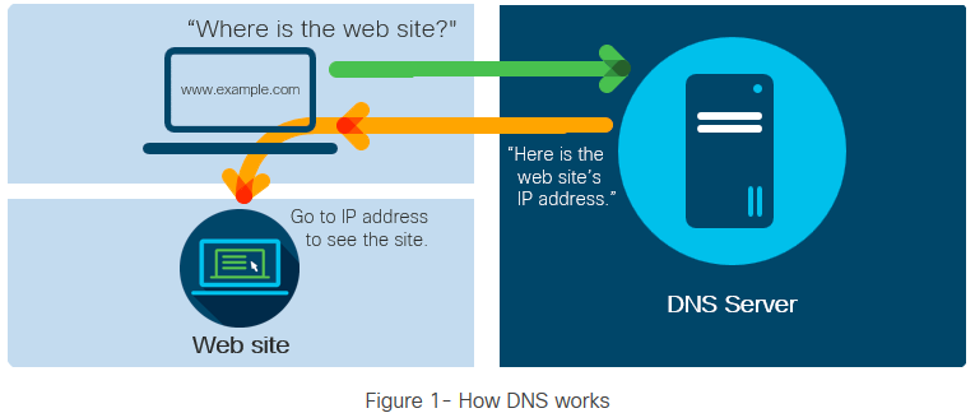
DNS (ডোমেইন নেম সিস্টেম) আসলে কি? আসুন প্রযুক্তির সংক্ষিপ্ত কিছু ব্যাখ্যা দিয়ে শুরু করা যাক। ডোমেন নেম সিস্টেম (ডিএনএস) হল এমন একটা প্রযুক্তি যা ইন্টারনেট ব্যবহারকারীদের বিভিন্ন ওয়েবসাইট এবং ইন্টারনেটের অন্যান্য স্থানে পরিচালিত করে। উদাহরণস্বরূপ আপনার মোবাইলের ফোন বুক এর এন্ট্রিকে ধরা যেতে পারে যেখানে আমরা প্রত্যেকটি নাম্বার এর স্থানে ব্যক্তি বিশেষের নাম দিয়ে শনাক্ত করে থাকি। একইভাবে ডিএনএস এর রেকর্ডগুলি পরীক্ষা করে এবং তারপরে...
Read More
Description : Multiple vulnerabilities were identified in Google Chrome, a remote attacker could exploit some of these vulnerabilities to trigger remote code execution and security restriction bypass on the targeted system. Impact: Remote Code Execution Security Restriction Bypass System / Technologies Affected : Google Chrome (Desktop version) prior to 80.0.3987.132 Mitigation: Before installation of the software, please visit the vendor’s web-site for more details....
Read More
Description: A vulnerability has been discovered in the WordPress Duplicator Plugin that could allow for Arbitrary File Downloads. This vulnerability exists due to the way Duplicator handles certain requests from unauthenticated users. When an attacker sends a specially crafted request to Duplicator, an unauthenticated user can download arbitrary files from the target WordPress site. This includes the ‘wp-config.php’ file, which contains various site configurations, and...
Read More
Subject: A Vulnerability in Apache Tomcat Could Allow for Arbitrary File Reading (CVE-2020-1938) Description: A vulnerability has been discovered in Apache Tomcat, which could allow for reading of arbitrary files on the affected system. The vulnerability exists in the AJP protocol, which is by default exposed over TCP port 8009 and enabled. The vulnerability can be exploited by an attacker who can communicate with...
Read More
The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures. The National Cybersecurity FFRDC, operated by the Mitre Corporation, maintains the system, with funding from the National Cyber Security Division of the United States Department of Homeland Security. Report : Following is the CVE report from BGD e-GOV CIRT for the month of February 2020.
MITRE has released version 4.0 of the community-developed Common Weakness Enumeration (CWE) list. Previous CWE list versions describe common software security weaknesses. With version 4.0, the CWE list expands to include hardware security weaknesses. Additionally, version 4.0 simplifies the presentation of weaknesses into various views and adds a search function to enable easier navigation of the information. The CWE List of Common Security Weaknesses can...
Read More
Description: Google has released Chrome version 80.0.3987.122 for Windows, Mac, and Linux. This version addresses vulnerabilities that an attacker could exploit to take control of an affected system. Impact: A remote attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://chromereleases.googleblog.com/2020/02/stable-channel-update-for-desktop_24.html
The Effect of Geopolitics on Cybersecurity Technological growth and its breakthrough advances, along with their advantages, also have disadvantages, which are obvious examples of communication equipment. In fact, today, the Internet, telephones, cell phones and other communication devices can be described as a double-edged sword used to facilitate communications on the one hand and to spy on and monitor information. The main pillar of cyber...
Read More
Description: Microsoft has released updates to address multiple vulnerabilities in Microsoft software. A remote attacker could exploit some of these vulnerabilities to take control of an affected system. Impact: A remote attacker could exploit this vulnerability to take control of an affected system. Mitigation: Updates are available. Please see the references or vendor advisory for more information. Reference URL’s: https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Feb https://support.microsoft.com/en-us/help/20200211/security-update-deployment-information-february-11-2020