in Security Advisories & Alerts
Multiple Vulnerabilities in SAP Products Could Allow for Arbitrary Code Execution
DESCRIPTIONMultiple vulnerabilities have been discovered in SAP products, the most severe of which could allow an unauthenticated, remote attacker to execute code on the affected systems. Details of the vulnerabilities are as follows: * Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard) (CVE-2020-6286).* Security updates for the browser control Google Chromium delivered with SAP Business Client.* Information Disclosure in SAP NetWeaver (XMLToolkit for...
Read More
in Articles, English articles, News
5W & 1H of Phishing Campaign
A phishing campaign is a kind of scam ran through email and intended to snip personal information from victims. Phishing basically depend on a vulnerability we can never fully abolish- human mistakes. The theme of the attack or the lure to attract human errors to commit the mistake depends on surroundings. For example, APWG or Anti Phishing Working Group Q1 2020 report states that cybercriminals...
Read More
in News Clipping
BlockThreat – Week 26, 2020
Another week, another DeFi exploit or two. Unfortunately, this time the bad folks were able to steal $500k worth of tokens. It’s too bad Balancer devs dismissed an earlier bug bounty report. ClearSky released a detailed report on CryptoCore APT which is dedicated to breaking into cryptocurrency exchanges. On a more fun side checkout someone almost getting caught by a honeypot smart contract and submit your...
Read More
in Security Advisories & Alerts
TMUI RCE vulnerability CVE-2020-5902
Description In BIG-IP versions 15.0.0-15.1.0.3, 14.1.0-14.1.2.5, 13.1.0-13.1.3.3, 12.1.0-12.1.5.1, and 11.6.1-11.6.5.1, the Traffic Management User Interface (TMUI), also referred to as the Configuration utility, has a Remote Code Execution (RCE) vulnerability in undisclosed pages. Impact This vulnerability allows for unauthenticated attackers, or authenticated users, with network access to the TMUI, through the BIG-IP management port and/or Self IPs, to execute arbitrary system commands, create or delete...
Read More
in Articles, Bangla Articles, News
অনিরাপদ ই-মেইল থেকে কিভাবে সুরক্ষিত থাকবেন
হ্যাকার, সাইবার অপরাধী এবং অন্যান্য অনলাইন দুষ্কৃতীদের জন্য ই-মেইল, সাইবার আক্রমণের একটি বিশেষ হাতিয়ার। বর্তমানে বেশির ভাগ সংস্থাগুলো যোগাযোগের প্রাথমিক মাধ্যম হিসাবে ই-মেইল ব্যবহার করে। সংস্থাগুলো অজ্ঞাতসারে তথ্য লঙ্ঘনের (data breaches) শিকার হতে পারে যদি তাদের কোন কর্মী অনিচ্ছাকৃত ভাবে ই-মেইলের কোন অনিরাপদ সংযুক্তি (attachment) ডাউনলোড করেন বা দূষিত লিঙ্ক (link) ক্লিক করেন। ব্যবহারকারীরা প্রতিদিন অসংখ্য ই-মেইল পান যাতে কিছু স্প্যাম ই-মেইল থাকে। ব্যবহারকারী যদি...
Read More
in CVE, Security Advisories & Alerts
Common Vulnerabilities and Exposures (CVE) Report June 2020
The Common Vulnerabilities and Exposures (CVE) system provides a reference-method for publicly known information-security vulnerabilities and exposures. The National Cybersecurity FFRDC, operated by the Mitre Corporation, maintains the system, with funding from the National Cyber Security Division of the United States Department of Homeland Security. Report : Following is the CVE report from BGD e-GOV CIRT for the month of June 2020.
in Articles, English articles, News
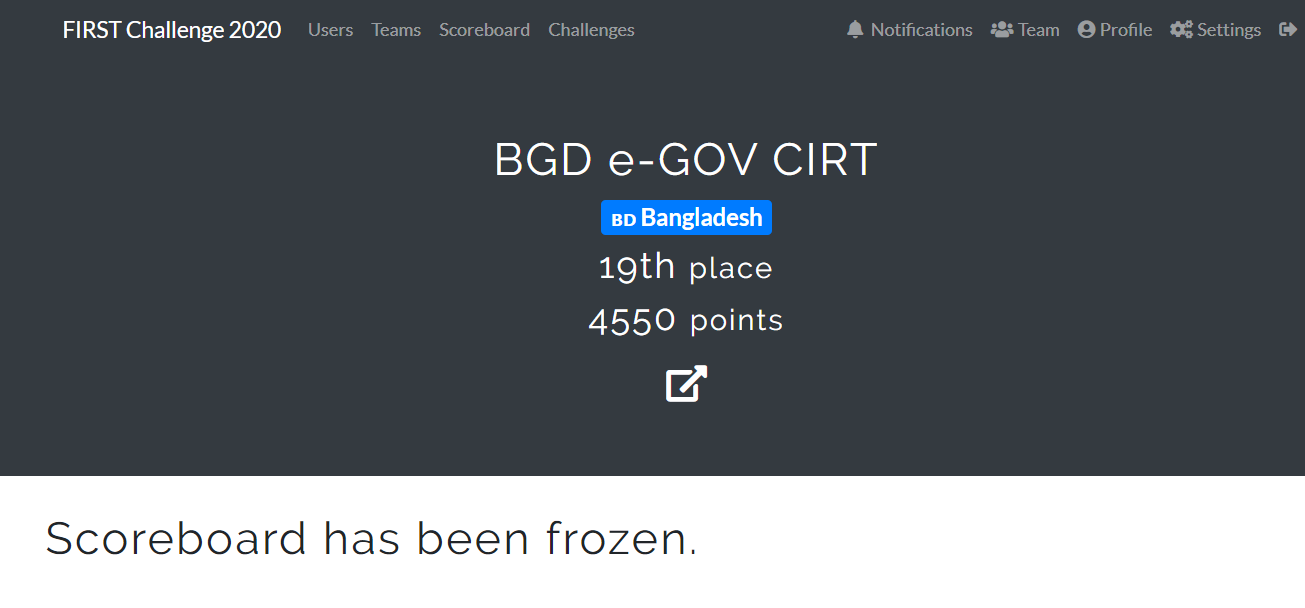
FIRST Annual CTF-2020: BGD e-Gov CIRT Secured 19th Place
As being a full member of FIRST, Bangladesh Government’s Cyber Security unit BGD e-GOV CIRT took part in annual CTF and achieved 19th position among 278 teams from all over the world. FIRST is the global Forum of Incident Response and Security Teams. It is an international confederation of trusted computer incident response teams who cooperatively handle computer security incidents and promote incident prevention programs. It...
Read More
in Security Advisories & Alerts
SaltStack Patches Critical Vulnerabilities in Salt
SaltStack has released a security update to address critical vulnerabilities affecting Salt versions prior to 2019.2.4 and 3000.2. Salt is an open-source remote task and configuration management framework widely used in data centers and cloud servers. A remote attacker could exploit these vulnerabilities to take control of an affected system. These vulnerabilities were detected in exploits in the wild. CVE-2020-11651: An issue was discovered in...
Read More
in Security Advisories & Alerts
ISC Releases Security Advisories for BIND
CVE-2020-8618:An assertion check in BIND (that is meant to prevent going beyond the end of a buffer when processing incoming data) can be incorrectly triggered by a large response during zone transfer. Impact: An attacker who is permitted to send zone data to a server via zone transfer can exploit this to intentionally trigger the assertion failure with a specially constructed zone, denying service to...
Read More