DESCRIPTIONA vulnerability has been discovered in Adobe Flash Player, which could allow for arbitrary code execution. Adobe Flash Player is a widely distributed multimedia and application player used to enhance the user experience when visiting web pages or reading email messages. Successful exploitation of this vulnerability could result in an attacker executing arbitrary code in the context of the affected application. Depending on the privileges...
Read More
DESCRIPTION Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Google Chrome is a web browser used to access the Internet. Successful exploitation of the most severe of these vulnerabilities could allow an attacker to execute arbitrary code in the context of the browser. Depending on the privileges associated with the application, an attacker could...
Read More
DESCRIPTIONMultiple vulnerabilities have been discovered in the Google Android operating system (OS), the most severe of which could allow for remote code execution. Android is an operating system developed by Google for mobile devices, including, but not limited to, smartphones, tablets, and watches. Successful exploitation of the most severe of these vulnerabilities could allow for remote code execution within the context of a privileged process....
Read More
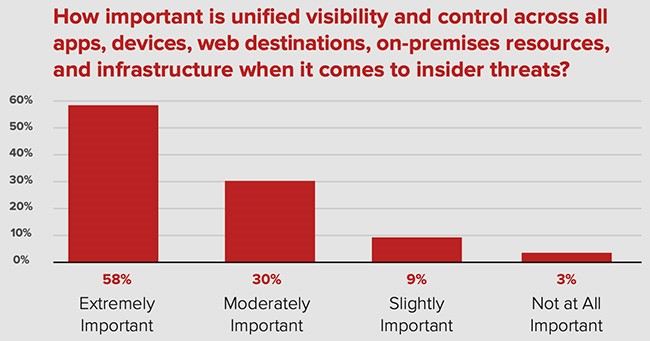
সাইবার জগতে অভ্যন্তরীণ আক্রমণ একটি ভয়ানক হুমকির নাম। প্রতিষ্ঠানে চাকুরীরত কর্মকর্তা-কর্মচারীদের কোন একজনের অবহেলা বা অসতর্কভাবে ডিজিটাল ডিভাইস বা যন্ত্রপাতির ব্যবহার বা ক্ষতিকারক (ম্যালিশিয়াস) কর্মকানন্ডের প্রেক্ষিতে প্রতিষ্ঠানকে সাইবার আক্রমনের স্বীকার হতে হয় এবং সমূহ ক্ষতির সম্মুখীন হতে হয়। বিটগ্লাস কর্তৃক সম্পাদিত একটি জরিপ প্রতিবেদন অনুযায়ী বিগত ১২ মাসে বিভিন্ন প্রতিষ্ঠানে সংঘটিত সাইবার আক্রমণগুলোর আনুমানিক ৬১% এর সাথে সেই প্রতিষ্ঠানেরই আভ্যন্তরীণ কর্মকর্তা-কর্মচারী জড়িত ছিলেন। আভ্যন্তরীণ হুমকিগুলোর...
Read More
DESCRIPTIONTreck IP network stack software is designed for and used in a variety of embedded systems. The software can be licensed and integrated in various ways, including compiled from source, licensed for modification and reuse and finally as a dynamic or static linked library. Treck IP software contains multiple vulnerabilities, most of which are caused by memory management bugs. For more details on the vulnerabilities...
Read More
Introduction Fileless malware attack is on the rise, and it’s one of the foremost important digital infiltration threats to companies, according to Symantec’s 2019 Internet Security Threat Report. The magnitude of this threat is usually seen within the Report’s finding that malicious PowerShell scripts — one of the key components of fileless malware attacks — increased quite 1,000 percent in 2018 and accounted for 89...
Read More
DESCRIPTION Multiple vulnerabilities have been discovered in Microsoft Edge, the most severe of which could allow for arbitrary code execution. Microsoft Edge is a web browser used to access the Internet. Successful exploitation of the most severe of these vulnerabilities could allow an attacker to execute arbitrary code in the context of the browser. Depending on the privileges associated with the application, an attacker could...
Read More
DESCRIPTION Multiple vulnerabilities have been discovered in iCloud for Windows and macOS. The most severe of these vulnerabilities could allow for arbitrary code execution. macOS is a desktop operating system for Macintosh computers. iCloud is a cloud storage service that can be used on Windows computers. Successful exploitation of the most severe of these vulnerabilities could result in arbitrary code execution within the context of...
Read More