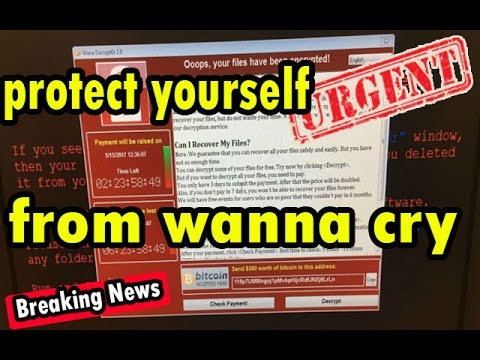
বর্তমানে বিশ্বের অনেক দেশে WannaCry র্যানসমওয়্যার দ্বারা আক্রমণের শিকার হয়েছে। এই বিষয়ে কিছু তথ্য নিচে দেওয়া হল WannaCry প্রথমিক লক্ষ্য মাইক্রোসফটের অপারেটিং সিস্টেম উইন্ডোজ চালিত কম্পিউটার অ্যাটাক করা যাতে MS17-010 প্যাচ (Patch) দেয়া নেই তাৎক্ষনিক করনীয় মাইক্রোসফটের অপারেটিং সিস্টেম উইন্ডোজ চালিত অনাক্রান্ত কম্পিউটার এ MS17-010 প্যাচ (Patch) দিয়ে হালনাগাদ করে নিতে হবে। WannaCry র্যানসমওয়্যার কিভাবে নেটওয়ার্ক এ আক্রমণ করে? সাধারণত কম্পিউটার ব্যবহারকারী যদি কোন স্প্যাম ইমেইল থেকে কোন...
Read More
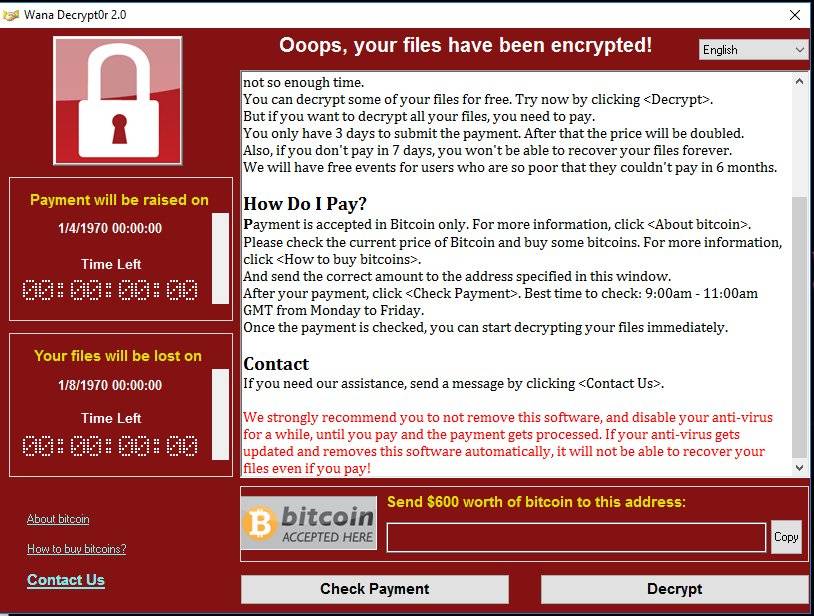
A massive ransomware attack affected computer systems across the world. Security researchers say it is a Windows exploit first developed by the United States National Security Agency, shut down computer systems across several countries. It has hit computer systems of hundreds of private companies and public organizations across the globe which is being called as WannaCry (also known as ‘Wana Decrypt0r,’ ‘WannaCryptor’ or ‘WCRY’). Like...
Read More
Description: WordPress through 4.7.4 relies on the Host HTTP header for a password-reset e-mail message, which makes it easier for remote attackers to reset arbitrary passwords by making a crafted wp-login.php?action=lostpassword request and then arranging for this message to bounce or be resent, leading to transmission of the reset key to a mailbox on an attacker-controlled SMTP server. This is related to problematic use of...
Read More
Description: Microsoft Windows SMB Server is prone to a remote code-execution vulnerability. Successful exploits will allow an attacker to execute arbitrary code on the target system. Failed attacks will cause denial of service conditions. Related CVE’s: CVE-2017-0145, CVE-2017-0146, CVE-2017-0147, CVE-2017-0148 Vulnerable Versions: Microsoft Windows Vista x64 Edition Service Pack 2 Microsoft Windows Vista Service Pack 2 Microsoft Windows Server 2012 R2 Microsoft Windows Server 2012...
Read More
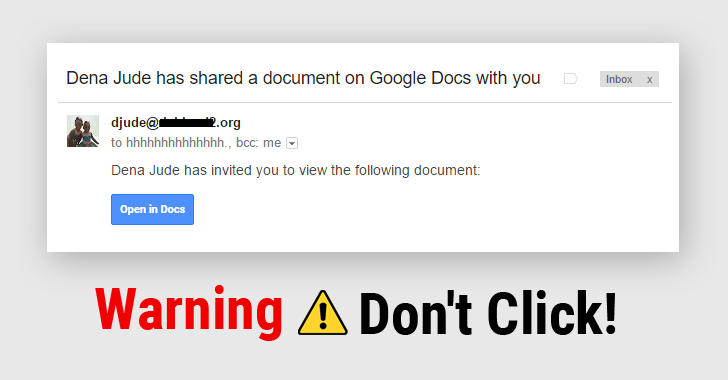
A piece of malware is going around that pretends to be a Google Docs link which is a phishing scheme is racing around the internet right now, which means you should avoid clicking any weird Google Docs that have been emailed to you recently — even if it’s from someone you know. It’s spreading incredibly quickly. If you click the link, it asks for some...
Read More
Description: SquirrelMail versions 1.4.22 and below are vulnerable to a command-line argument injection exploit that could allow arbitrary code execution if $edit_identity and $useSendmail are enabled and user has knowledge of the location and permissions on the SquirrelMail attachment directory. Impact: Successful exploit allows an attacker to inject and execute arbitrary commands in context of the affected application. Squirrelmail version 1.4.22 and prior are vulnerable....
Read More
Description: The NFSv2 and NFSv3 server implementations in the Linux kernel through 4.10.13 lacks certain checks for the end of a buffer, which allows remote attackers to trigger pointer-arithmetic errors or possibly have unspecified other impact via crafted requests, related to fs/nfsd/nfs3xdr.c and fs/nfsd/nfsxdr.c. Impact: Attackers can exploit these issues to bypass certain security restrictions and perform unauthorized actions. This may aid in further attacks....
Read More