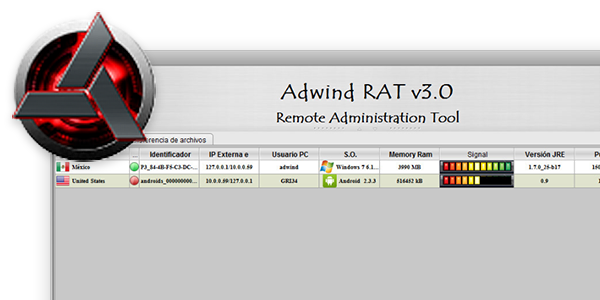
Threat Level Medium Security experts at TrendMicro discovered that the notorious Adwind RAT has resurfaced targeting enterprises in the Aerospace industries worldwide. Adwind is a cross-platform Remote Access Trojan written in Java, it was detected recently in attacks against aerospace enterprises in Switzerland, Austria, Ukraine, and the US. The Adwind RAT was first discovered early 2012, the experts dubbed it Frutas RAT and later it was identified with...
Read More
Description: Win32k in Microsoft Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, and 1703, and Windows Server 2016 allows an elevation of privilege vulnerability when it fails to properly handle objects in memory, aka “Win32k Elevation of Privilege Vulnerability”. This CVE ID is unique from CVE-2017-8578, CVE-2017-8580,...
Read More
Description: Graphics in Microsoft Windows 7 SP1, Windows Server 2008 SP2 and R2 SP1, Windows 8.1 and Windows RT 8.1, Windows Server 2012 and R2, Windows 10 Gold, 1511, 1607, 1703, and Windows Server 2016 allows an elevation of privilege vulnerability due to the way it handles objects in memory, aka “Win32k Elevation of Privilege Vulnerability”. Impact: A local attacker can exploit this issue to...
Read More
Description: Windows kernel in Microsoft Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, and 1703, and Windows Server 2016 allows an elevation of privilege vulnerability due to the way it handles objects in memory, aka “Windows Kernel Elevation of Privilege Vulnerability”. Impact: An attacker can exploit this issue to execute arbitrary code with elevated privileges. Mitigation: Updates...
Read More
Description: Microsoft WordPad in Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, 1703, and Windows Server 2016 allows a remote code execution vulnerability due to the way it parses specially crafted files, aka “WordPad Remote Code Execution Vulnerability”. Impact: Successfully exploiting this issue may result in the...
Read More
Description: Microsoft Windows 7 SP1, Windows Server 2008 SP2 and R2 SP1, Windows 8.1 and Windows RT 8.1, Windows Server 2012 and R2, Windows 10 Gold, 1511, 1607, 1703, and Windows Server 2016 allows a remote code execution vulnerability due to the way that Windows Search handles objects in memory, aka “Windows Search Remote Code Execution Vulnerability”. Impact: Successfully exploiting this issue may result in...
Read More
Description: Windows PowerShell in Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, 1703, and Windows Server 2016 allows a remote code execution vulnerability when PSObject wraps a CIM Instance, aka “Windows PowerShell Remote Code Execution Vulnerability”. Impact: Successfully exploiting this issue may result in the execution of...
Read More
Description: Microsoft Edge in Windows 10 1703 allows a remote code execution vulnerability in the way affected Microsoft scripting engines render when handling objects in memory, aka “Microsoft Edge Remote Code Execution Vulnerability.” Impact: Attackers can exploit this issue to execute arbitrary code in the context of the currently logged-in user. Failed attacks will cause denial of service conditions. Mitigation: Updates are available. Please check...
Read More
Description: HTTP.sys in Microsoft Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, 1607, and 1703, and Windows Server 2016 allows an information disclosure vulnerability when the component improperly handles objects in memory, aka “Https.sys Information Disclosure Vulnerability”. Impact: Attackers can exploit this issue to obtain sensitive information that...
Read More
Description: Microsoft .NET Framework 4.6, 4.6.1, 4.6.2, and 4.7 allow an attacker to send specially crafted requests to a .NET web application, resulting in denial of service, aka .NET Denial of Service Vulnerability. Impact: Denial of Service Vulnerability Mitigation: Updates are available. Please check specific vendor advisory for more information. Reference URL’s: http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=2017-8585 https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-8585