An authentication bypass Zimbra security vulnerability is actively exploited to compromise Zimbra Collaboration Suite (ZCS) email servers worldwide.According to threat intelligence firm Volexity, attackers have been abusing a ZCS remote code execution flaw tracked as CVE-2022-27925 requiring authentication with the help of an auth bypass bug (tracked as CVE-2022-37042). Description: CVE-2022-27925: Zimbra Collaboration (aka ZCS) 8.8.15 and 9.0 has mboximport functionality that receives a ZIP...
Read More
বিজিডি ই-গভ সার্ট -এর বাৎসরিক নিয়মিত বিভিন্ন সাইবার ড্রিল আয়োজনের পরিকল্পনা অনুসারে ২৩-২৪ আগস্ট ২০২২ তারিখে দুইদিন ব্যাপী আন্ত:বিশ্ববিদ্যালয় সাইবার ড্রিল ২০২২ অনুষ্ঠিত হয়। এ সাইবার ড্রিলে যোগ দেয়ার জন্য ৫৮টি টিম রেজিস্ট্রেশন করে এবং মোট ২৬৮ জন শিক্ষার্থী সক্রিয়ভাবে অংশগ্রহণ করে। দেশের বিভিন্ন বিশ্ববিদ্যালয়ের শিক্ষার্থীরা দলগতভাবে এ প্রতিযোগিতায় অংশ নেয়। ইসলামিক ইউনিভার্সিটি অফ টেকনোলজি -এর ‘আই ইউ টি জেনেসিস’ (IUT GENESIS) টিম সর্বমোট ৫৫০০...
Read More
অদ্য ১লা আগস্ট, ২০২২ (সোমবার) তারিখে বিজ্ঞান ও প্রযুক্তি মন্ত্রনালয়ের মাননীয় মন্ত্রী স্থপতি জনাব ইয়াফেস ওসমান বিজিডি ই-গভ সার্ট -এর কার্যালয় পরিদর্শন করেন। তিনি সিকিউরিটি অপারেশন সেন্টার (SOC) সহ বিজিডি ই-গভ সার্ট প্রকল্পের বিভিন্ন কম্পোনেন্ট এর কার্যক্রম ঘুরে দেখেন। প্রকল্প পরিচালক জনাব তারেক এম. বরকতউল্লাহ, পরিচালক (সিএ অপারেশন ও নিরাপত্তা এবং জাতীয় ডাটা সেন্টার), বাংলাদেশ কম্পিউটার কাউন্সিল মাননীয় মন্ত্রীকে বিজিডি ই-গভ সার্ট -এর বিভিন্ন কার্যক্রম...
Read More
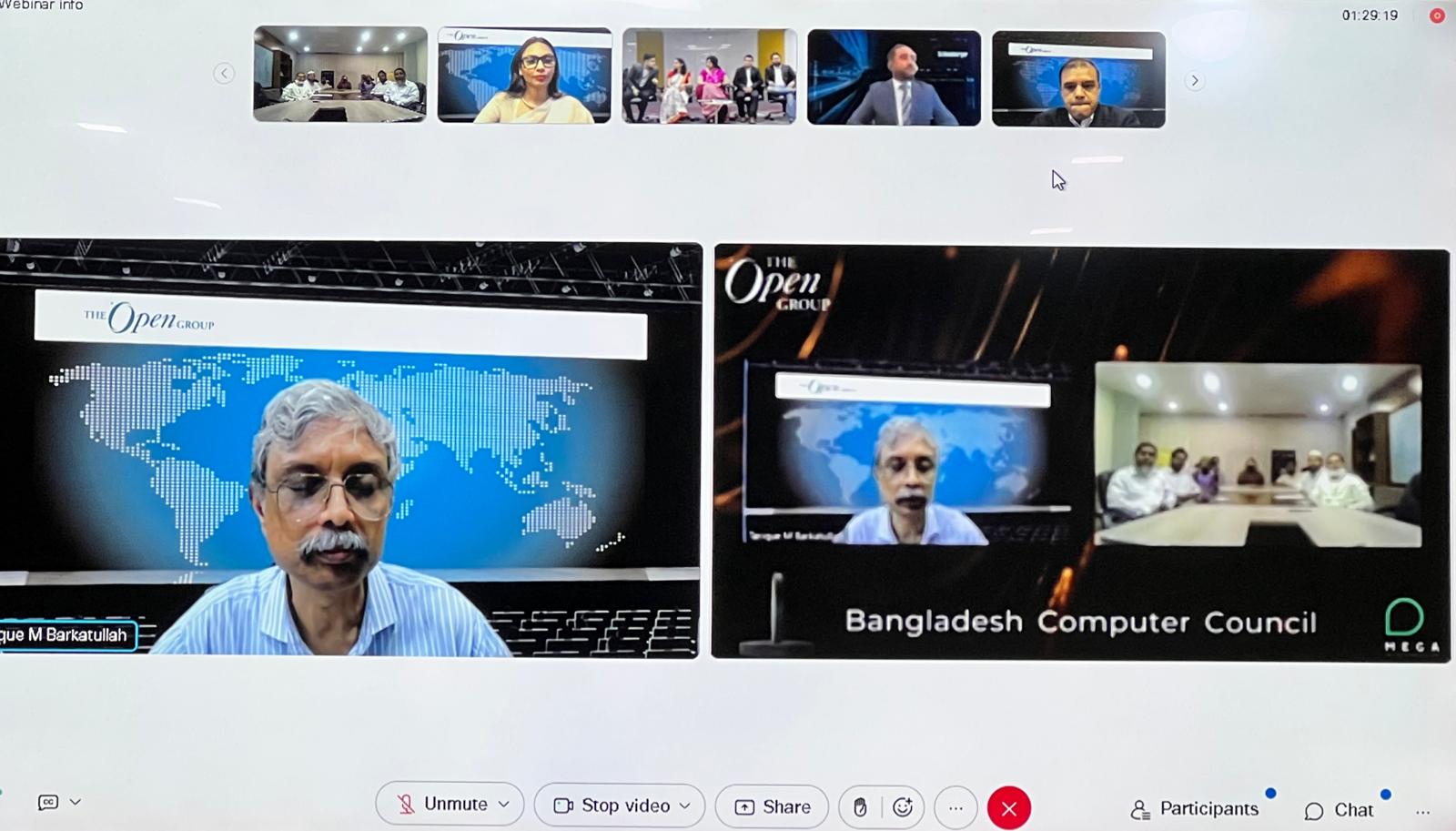
Bangladesh Computer Council (BCC) has won “The Award of Distinction in Digital Innovation” in the category of TOGAF standard / Enterprise Architecture from the Open Group, India for the year 2022 for establishing National e-Service Bus. The Open Group India Awards recognizes organizations and teams in the Southeast Asia region that have reached the pinnacle of achievement in applying standards, open-source software, and best practices in Enterprise...
Read More
BGD e-GOV CIRT গত বছরের মত এবারও সকল বিশ্ববিদ্যালয়ের শিক্ষার্থীদের অংশগ্রহণের মাধ্যমে তাদের দক্ষতা বৃদ্ধি ও সাইবার নিরাপত্তার ধারণা দেওয়ার জন্য আগামী ২৩-২৪ আগস্ট ২০২২ তারিখে দুইদিন ব্যাপী University Cyber Drill 2022 আয়োজন করতে যাচ্ছে। এই প্রতিযোগিতায় অংশগ্রহন করতে প্রথমে Registration করে টীম তৈরী করতে হবে। Registration এর জন্য একটি গাইডলাইন এবং প্রতিযোগিতায় অংশগ্রহনের Rules of engagement প্রস্তুত করে CIRT এর ওয়েবসাইটে publish করা হয়েছে।...
Read More
Description:kernel/bpf/verifier.c in the Linux kernel through 5.15.14 allows local users to gain privileges because of the availability of pointer arithmetic via certain *_OR_NULL pointer types. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. Impact: A local attacker may exploit this issue to gain elevated root privileges on the affected system. Mitigation: Updates...
Read More
Microsoft has released updates to address multiple vulnerabilities in Microsoft software. An attacker can exploit some of these vulnerabilities to take control of an affected system. CVE-2022-30190, also known as “Follina” — the RCE vulnerability in the Microsoft Windows Support Diagnostic Tool that was disclosed in late May and exploited in the wild — has now received patches for affected Windows systems. While Microsoft had...
Read More
Security researchers have discovered a new Microsoft Office zero-day vulnerability that is being used in attacks to execute maliciously PowerShell commands via Microsoft Diagnostic Tool (MSDT) simply by opening a Word document. Workarounds: In Microsoft Defender’s Attack Surface Reduction (ASR) activating the rule “Block all Office applications from creating child processes” in Block mode will prevent this from being exploited.[https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide#block-all-office-applications-from-creating-child-processes] Disable the MSDT URL Protocol....
Read More